
Menu
Blog

Larger than WannaCry: EternalRocks Worm Spreads Using 7 Leaked NSA Exploits
Blog
2 minutes
May 24, 2017
A new worm, EternalRocks that exploits Windows SMB (Server Message Block) vulnerabilities has been discovered by a security researcher. EternalRocks uses seven SMB-specific NSA tools, while WannaCry used only two. It is ...
By:
SCA Editor
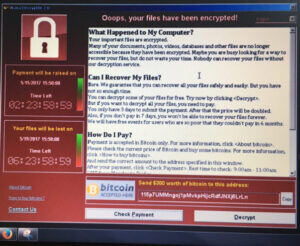
What is WannaCry, WannaCrypt, WanaCrypt0r 2.0, Wanna Decryptor and how to Protect Yourself from Ransomware
Blog
3 minutes
May 17, 2017
[vc_section css=”.vc_custom_1511863100091{margin-right: 0px !important;}”][vc_row css=”.vc_custom_1510315062002{margin-top: 0px !important;margin-bottom: 30px !important;padding-top: 0px !important;padding-bottom: 0px ...
By:
SCA Editor
NCUA Examiner Insight for 2017
Blog
2 minutes
March 01, 2017
The 12th annual CUISPA (Credit Union Information Security Professionals Association) conference was held on February 21 & 22 in San Antonio. SCA routinely participates in this conference to network with credit union ...
By:
SCA Editor
Washington State DCU Selects SCA to Deliver IT Examinations
Blog
3 minutes
January 13, 2016
[vc_row][vc_column][vc_column_text] CLEARWATER, FL (December 17, 2015) — Security Compliance Associates (SCA) is pleased to announce that the company has recently been awarded as the primary vendor to assist in the ...
By:
SCA Editor

Vulnerability Scan vs. Pen Test – What’s the Difference?
Blog
3 minutes
September 02, 2015
By:
SCA Editor

Medical Records Worth More Than Credit Card Info
Blog
7 minutes
May 18, 2015
There has been a lot of information all over the news about recent large breaches in the healthcare industry. Millions of individuals have been affected by these breaches in the healthcare industry. The healthcare ...
By:
SCA Editor
SCA Announces Strategic Partnership With Fidelity National Title Group
Blog
2 minutes
September 05, 2014
[vc_row][vc_column][vc_column_text] Security Compliance Associates Announces Newest Strategic Partner For Immediate Release Growth in Title & Settlement Sector for Information Security Services Fuels Fidelity ...
By:
SCA Editor

Technical Vulnerability Scan is a REQUIREMENT for HIPAA Security Risk Assessments and Meaningful Use Security Risk Analysis
Blog
2 minutes
August 13, 2014
After being asked on numerous occasions if technical vulnerability scans are required or if a checklist will suffice repeatedly by practices I felt it would be worthwhile to see if there is another way for me to ...
By:
SCA Editor
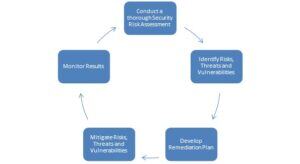
HIPAA Security Risk Assessment Key Points to Remember
Blog
5 minutes
July 17, 2014
I have been asked many times in the past few months, what constitutes a Risk Assessment? Is there a checklist I can follow? Does the tool on http://www.healthit.gov/providers-professionals/security-risk-assessment-tool ...
By:
SCA Editor
Florida’s New Data Privacy, Security and Breach Notification Law Effective July 1st, 2014
Blog
2 minutes
July 01, 2014
[vc_row][vc_column][vc_column_text] The “Florida Information Protection Act of 2014” (FIPA) was signed into law by Florida Governor Rick Scott on June 20, 2014 and takes effect on July 1st, 2014. With overwhelming ...
By:
SCA Editor